One, product introduction
Internal and external network physical isolation to ensure the safety of the connection, but between inner and outer net necessary data exchange difficult. Use of mobile storage copy and copy CD way there were operating inconvenience, management complex, also cannot avoid Trojan ferry attack threat.
Ferry equipment deployment in between inner and outer net and provides customers with a kind of physical isolation between inner and outer net (or high and low security network between the external data file unidirectional safely into the internal network solutions so as to realize safe and efficient data exchange, effectively eliminate the Trojan ferry attacks, prevent the connection leak.
Two, the product features
(1) safety isolation, file unidirectional ferry, prevent the internal data were leaked
System USES "2 + 1" (internal and external host + special light unidirectional isolation hardware) system architecture, realize the internal and external network safe isolation premise file unidirectional ferry to ensure data "only into a", to prevent internal data were leaked.
(2) support file virus killing, file signature verification, improve the overall level of security
Support virus characteristics, heuristic killing, and through the signature verification to ensure that only conform to the rules of signature verification documents ferry, realize reliable file as needed through the security goal.
(3) support mass data multitasking, high performance and real-time ferry, improve work efficiency
Support mass data multitasking priority function, make sure the important data first ferry, and achieve the industry's leading one billion line speed performance, solve the unidirectional transmission performance bottleneck, ensure file real-time ferry.
(4) platform change management
Product support access "unified security platform", through the platform to provide strategy management, correlation analysis, such as situation awareness of security mechanism, realize "platform is changed, intelligent" safety management, improve the efficiency of security management, improve the comprehensive protection ability.
(5) cloud protection mechanism
Product support access "cloud security center", the use of center provides real-time monitoring, intelligent security, dynamic strategy of security mechanism, realize "cloud protection" security goals, improve safety equipment protection efficiency and protection ability.
Three, typical deployment
A unit inside and outside network physical isolation, need two kinds of data safety, high efficiency into a network, including from other department for business data, from the Internet access system patch, virus upgrade library system data.
The deployment of an artificial copy terminals, mobile storage media copy business data, and then through the ferry equipment unidirectional introduction to the connection; The deployment of a automatic receiving server, from the Internet to be automatic collection system data, and then through the ferry equipment unidirectional introduction to the connection.
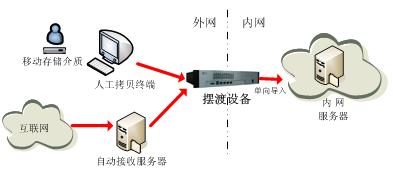 The scheme to solve the network isolation and data security exchange problem, not only achieve a variety of data, various ways of safe and efficient network into, and effective to eliminate Trojan ferry attacks, prevent network leak QieMi occurrences.
The scheme to solve the network isolation and data security exchange problem, not only achieve a variety of data, various ways of safe and efficient network into, and effective to eliminate Trojan ferry attacks, prevent network leak QieMi occurrences.