One, product introduction
Some enterprises are facing the internal resources are illegal access, sensitive information is trojans steal, staff work time of the Internet, network congestion, Internet turtle speed and so on, and these will seriously affect the normal work of the enterprise, the launch of the brings to the enterprise loss.
The application of boundary protective equipment identification, network behavior analysis, intelligent flow control, special attack detection technology, strengthen the enterprise LAN and LAN, LAN and Internet network behavior between the management and control, so that all flow all can positioning to specific user and application, make sure the important data can be priority through, to prevent unauthorized access, illegal Internet, Trojan QieMi the occurrence of events such as, for the enterprise to create a safe and controllable network environment.
Two, the product features
(1) application identification
Product USES DPI (deep packet inspection) + DFI (depth flow detection) comprehensive application identification technology, can identify more than 1000 kinds of common network applications. Support through the WEB Portal, USB Key, LDAP, Radius and so on many kinds of ways to identify users identity, making the network traffic can be positioned to specific users and subordinate application, greatly improving the flow of transparency.
(2) the network behavior analysis
Product analysis, database file server, WEB, E-mail, and other key application protocol behavior, such as analysis the users access to the database which form, access to the file server which documents, analysis the user access to the WEB site, and what in particular on the BBS Posting behavior, the administrator can on-demand configuration safety rules, further standardize the user's network behavior, prevent unauthorized access, illegal Internet security incident, etc.
At the same time in visual way to analyze the overall network behavior, help manager to the current network in the application and flow distribution network, this paper analyzes whether there are abnormal access behavior, timely find problems and alarm.
(3) intelligent flow control
Different application on bandwidth and delay requirements are different, the product through the intelligent flow control technology, guaranteed that the key applications (such as business procedures, database, remote maintenance, video conference system, etc.) bandwidth and delay, restrict or block low priority application flow.
(4) specific attack detection
This product through the ShellCode detection, fingerprint feature detection, behavior feature detection, and other technical testing network attack, effectively block the worm propagation, trojans QieMi attacks, protect the network security, preventing the internal data leakage.
(5) platform change management
Product support access "unified security platform", through the platform to provide strategy management, correlation analysis, such as situation awareness of security mechanism, realize "platform is changed, intelligent" safety management, improve the efficiency of security management, improve the comprehensive protection ability.
(6) cloud protection mechanism
Product support access "cloud security center", the use of center provides real-time monitoring, intelligent security, dynamic strategy of security mechanism, realize "cloud protection" security goals, improve safety equipment protection efficiency and protection ability.
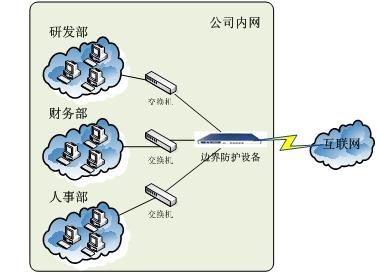
Three, typical deployment
Boundary protective equipment can be deployed in different between enterprise local area network (LAN), to prevent unauthorized access to database and file servers and other sensitive resources behavior, blocking network worm attacks, prevent cross infection between LAN worm virus, and according to the actual need for bandwidth allocation, guarantee business procedures, database, remote maintenance, video conference, and other key application of bandwidth, ensure the normal work smoothly.

Boundary protective equipment can also be deployed in enterprise Internet exports, prevent the internal staff's illegal Internet behavior, such as limit employees go to work in time to browse non-working need web pages, playing online games, long time online chat, watch network video, online fry, etc, blocking outgoing illegal behavior, prevent employees on the Internet without approval by sensitive information; Prevent Trojan QieMi behavior, prevent commercial QieMi horse theft of enterprise internal confidential.